How’s that for a click-baity title?
In all seriousness, though, when you upload files to OneDrive, Microsoft scans their contents. When you think about it, this makes sense: At a minimum, Microsoft is doing some virus scanning, indexing, etc., which requires it to look at the contents of your files. I don’t think there’s anything malicious going on, but folks should be aware that it’s happening.
You might ask what exactly brought this revelation to mind? What caused me to suddenly think about this?
Well… After years of stubbornly sticking with local accounts only and refusing let Microsoft keep a copy of my Windows profile, documents, etc. in the cloud, I recently gave in and purchased a Microsoft 365 family subscription, and let Microsoft back up my Windows profile to OneDrive.
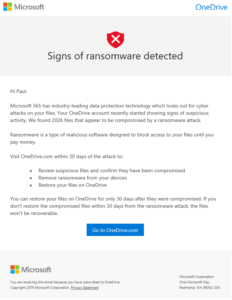 Shortly thereafter, I received an ominous e-mail from Microsoft. It started with a big red “X” and giant text reading “Signs of ransomware detected” and then went on to tell me that Microsoft had “found 2026 files that appear to be compromised by a ransomware attack.”
Shortly thereafter, I received an ominous e-mail from Microsoft. It started with a big red “X” and giant text reading “Signs of ransomware detected” and then went on to tell me that Microsoft had “found 2026 files that appear to be compromised by a ransomware attack.”
My immediate thought was that it must be a phishing attack of some sort that happened to be coincidentally well timed. Nope. All the links were to valid Microsoft URLs and they took me straight to Microsoft’s site without detouring to a login page where my credentials could be harvested.
So what on earth could have caused Microsoft to suddenly believe that I was the victim of a ransomware attack?
The e-mail was less than helpful, as it didn’t tell me what files it thought were victim to this ransomware attack, so I was left to figure out for myself what files it was flagging. Clearly, Microsoft was scanning my files, and had found a bunch of encrypted files, but what could those files be?
Suddenly a lightbulb went off in my head. You see, I use Cryptomator, which is a tool that allows you to maintain an encrypted vault of files. You mount the vault on a drive letter which then lets you transparently access unencrypted versions of the files for editing, etc., but all of the actual file storage remains encrypted. The encryption is all done locally on your system with a key that you provide, so the privacy of your data is never in the hands of anybody else.
In my case, I use this vault to store sensitive stuff like tax returns, bank account statements, scans of the family passports, etc.
The key thing, though, is that I had just synced a copy of my vault to OneDrive. Microsoft’s internal systems tried to open those files, found that they couldn’t, and went “Oh no! You must be the victim of a ransomware attack!” Nope. Sorry, Microsoft. Those are perfectly legitimate files that I deliberately encrypted because I don’t want you or anybody else to read them.
So what did I learn here?
- Microsoft opens your files and looks at what’s inside them.
- Microsoft can’t differentiate between files that you’ve deliberately encrypted and files that have been encrypted by ransomware (which is understandable, I suppose).
- When Microsoft finds files that it thinks are impacted by ransomware, it’ll tell you so, but won’t tell you which files it thinks are a problem.